MUMBAI, India, February 13, 2023 — Executive performance evaluations will be increasingly linked to ability to manage cyber risk; almost one-third of nations will regulate ransomware response within the next three years; and security platform consolidation will help organizations thrive in hostile environments, according to the top cybersecurity predictions revealed by Gartner, Inc.
In the opening keynote at the Gartner Security & Risk Management Summit in Mumbai, Deepti Gopal, Director Analyst and Christopher Mixter, VP Research at Gartner discussed the top predictions that security and risk management leaders should monitor to be successful in the digital era.
“The world around us is in turmoil, whether from economic, social, or geopolitical forces,” said Gopal. “Executives are expecting either substantial or significant industry transformation over the next five years. Now is the time for cybersecurity leaders to evaluate their current strategies and prepare to navigate the future with confidence.”
Gartner recommends that cybersecurity leaders use these strategic planning assumptions to influence their cybersecurity strategies for the coming years.
Cybersecurity Predictions
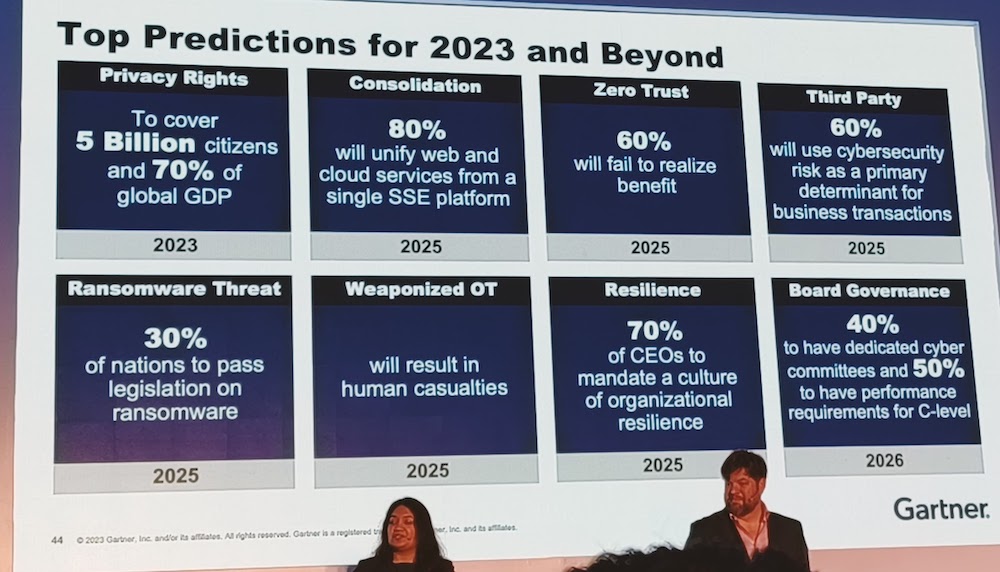
1. Privacy Rights: Through 2023, government regulations requiring organizations to provide consumer privacy rights will cover 5 billion citizens and more than 70% of global GDP.
The implications of new GDPR-centric privacy legislation mean organizations no longer have the luxury of only worrying about what’s stored in the country they’re operating in. Gartner analysts recommend that organizations develop a clear understanding of the privacy landscape, evaluate and introduce privacy enhancing computation to help preserve privacy and confidentiality via automation. They will also need to track subject rights request metrics to identify inefficiencies and justify accelerated automation.
2. Consolidation: By 2025, 80% of enterprises will adopt a strategy to unify web, cloud services and private application access from a single vendor’s SSE platform.
With a hybrid workforce and data everywhere accessible by everything, vendors are offering an integrated security service edge (SSE) solution to deliver consistent and simple web, private access and SaaS application security. Single-vendor solutions provide significant operational efficiency and security effectiveness compared with best-of-breed solutions, including tighter integration, fewer consoles to use, and fewer locations where data must be decrypted, inspected and re-encrypted.
3. Zero trust: 60% of organizations will embrace zero trust as a starting point for security by 2025. More than half will fail to realize the benefits.
The term zero trust is now prevalent in security vendor marketing and in security guidance from governments. As a mindset — replacing implicit trust with identity- and context-based risk appropriate trust — it is extremely powerful. However, as zero trust is both a security principle and an organizational vision, it requires a cultural shift and clear communication that ties it to business outcomes to achieve the benefits.
4. Third-party: By 2025, 60% of organizations will use cybersecurity risk as a primary determinant in conducting third-party transactions and business engagements.
Cyberattacks related to third parties are increasing. However, only 23% of security and risk leaders monitor third parties in real time for cybersecurity exposure, according to Gartner data. As a result of consumer concerns and interest from regulators, Gartner said organizations will start to mandate cybersecurity risk as a significant determinant when conducting business with third parties, ranging from simple monitoring of a critical technology supplier to complex due diligence for mergers and acquisitions.
5. Ransomware threat: Through 2025, 30% of nation states will pass legislation that regulates ransomware payments, fines and negotiations, up from less than 1% in 2021.
Modern ransomware gangs now steal data as well as encrypt it. The decision to pay the ransom or not is a business-level decision, not a security one. Gartner recommends engaging a professional incident response team as well as law enforcement and any regulatory body before negotiating.
6. Weaponized OT: By 2025, threat actors will have weaponized operational technology environments successfully to cause human casualties.
Attacks on OT – hardware and software that monitors or controls equipment, assets and processes – have become more common and more disruptive. In operational environments, security and risk management leaders should be more concerned about real world hazards to humans and the environment, rather than information theft, according to Gartner.
7. Resilience: By 2025, 70% of CEOs will mandate a culture of organizational resilience to survive coinciding threats from cybercrime, severe weather events, civil unrest and political instabilities.
The COVID-19 pandemic has exposed the inability of traditional business continuity management planning to support the organization’s response to a large-scale disruption. With continued disruption likely, Gartner recommends that risk leaders recognize organizational resilience as a strategic imperative and build an organization-wide resilience strategy that also engages staff, stakeholders, customers and suppliers.
8. Board Governance: By 2026, 50% of C-level executives will have performance requirements related to risk built into their employment contracts.
Most boards now regard cybersecurity as a business risk rather than solely a technical IT problem. As a result, Gartner analysts expect to see a shift in formal accountability for the treatment of cyber risks from the security leader to senior business leaders.
Learn more about the top technologies for security and risk in the complimentary Gartner webinar “The Gartner Emerging Technologies and Trends in Security and Risk for 2023.”