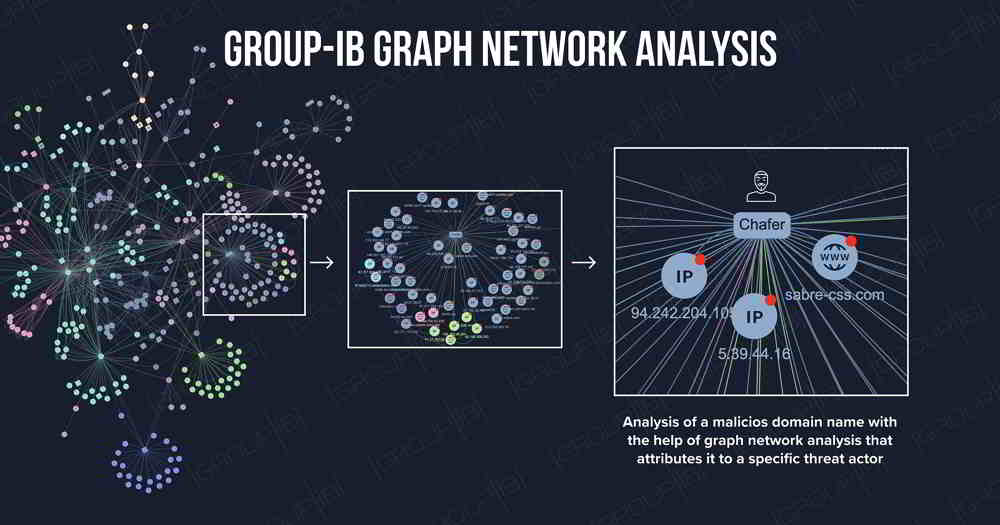
Group-IB, an international cybersecurity company that specializes in preventing cyberattacks, has launched a new tool for clients, which helps to predict and attribute attacks, even before they can occur. The Singapore-based company has granted its clients access to its internal tool for graph network analysis, which is capable of identifying links between scattered data, attributing an attack to a specific hacker group in seconds, as well as examine and predict possible threats that are relevant to a particular organization or industry.
Group-IB’s patented graph network analysis technologies are integrated in the company’s products, namely Threat Intelligence, Threat Detection System, Secure Bank and Brand Protection Service. The company’s decision to make its internal tool available to clients aims to help SOC and CERT analysts, threat intelligence experts and forensic researchers explore the tactics and infrastructure of the attackers, while at the same time improving their own cybersecurity systems and boosting their threat hunting skills.
Group-IB graph network analysis was designed based on indicators of compromise found during years of cybercrime investigations, incident response operations and malware analysis by Threat Intelligence and Threat Detection System. The historical data on cybercriminals, gathered in 16 years, includes billions of records from domain names, IP addresses, server digital fingerprints, which have been used in attacks, as well as tagging them to specific hackers or groups.
“It is nearly impossible to protect oneself against attacks and prevent possible damage without knowledge of their enemies,” commented Dmitry Volkov, Group-IB CTO and Head of Threat Intelligence. “We had considered dozens of graph network analysis providers before deciding to develop our own instrument. We did not find a single solution that met all our requirements. None of the graphs had the entire scope of historical data: domains, Passive DNS, Passive SSL, DNS records, open ports, services running on ports, and files that have connections with domain names and IP addresses. We started gathering such data records ourselves, updating them on an ongoing basis, with some of them covering a period of 15 years. We also did not like the fact that other solutions provided options only for manual graph creation, therefore, we built our graph to be completely automated. To tackle the problem of irrelevant links that is common for other products, we have taught our system to identify irrelevant links based on the logic of our experts who did it previously in manual mode. The main goal of our graph is threat hunting, the most accurate attribution and the deepest analysis of adversaries. This instrument is now available in our products.”
How Graph Network Analysis helps
Group-IB’s graph network analysis leaves unverified indicators of compromise behind and focuses on the attacker examination and threat management that are relevant to a particular business area. Analysts using Group-IB graph network analysis can type a suspicious domain, an IP address, email or SSL certificate fingerprint in the search bar, after which the system automatically creates a network graph based on the search element that shows linked domains, IP addresses, digital fingerprints and etc. Despite the fact that the majority of attackers – specifically cybercriminal and APT groups – try to remain undetected online, the majority of them have paid much less attention to their anonymity and operational security and resulting have made mistakes at the beginning of their criminal journey.
Graphs help to identify not only linked elements but also common features – patterns that characterize one specific cybercriminal group to another. The knowledge of such unique features helps to identify the elements of the attackers’ infrastructure at the attack preparation stage even without evidence confirming the attack such as phishing emails or malware.
For example, in December 2018, Cobalt hacker group, which is known for targeting banks, sent out emails disguised as the National Bank of Kazakhstan. If cybersecurity experts, for example, had not found the phishing emails and did not have an opportunity to carry out the comprehensive analysis of malicious files, they could have created a graph based on the malicious domain nationalbank[.]bz, used by the cybercriminals. The created graph would have immediately shown the links to other malicious domains and Cobalt cybercriminal group, revealing what files have already been used in earlier attacks.
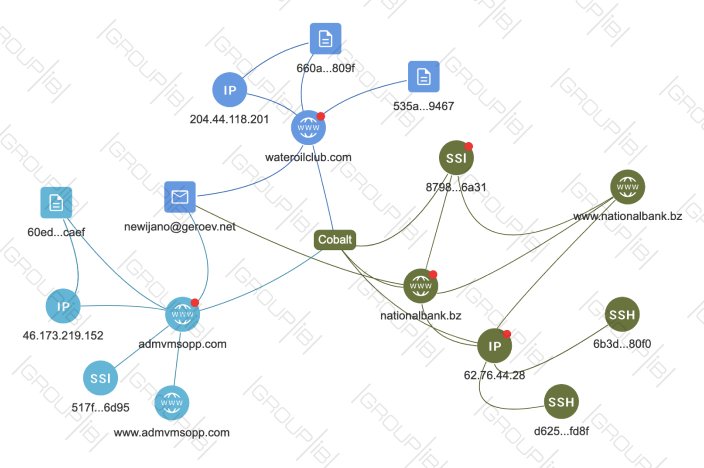
When Group-IB investigates phishing attacks, the activities of fake or pirate web sources, the company’s experts normally create graphs to identify linked web sources and check all the found hosts for analogous content. This enables Group-IB to find both old phishing pages, which remained active but undetected, and absolutely new phishing pages, which were created for future attacks and were not utilized so far.
Moreover, the graph network analysis is indispensable in searching for backends: 99 percent of cardshops, hacker forums, numerous phishing resources and other malicious servers are hiding both behind their own proxy servers and legitimate ones. The knowledge of the real location of a malicious server helps to identify the hosting service and create links to other malicious projects of the threat actors.
About Group-IB
Group-IB is a Singapore-based provider of solutions aimed at detection and prevention of cyberattacks, online fraud, IP protection and high-profile cyber investigations. Group-IB’s Threat Intelligence system has been named one of the best in class by Gartner, Forrester, and IDC. Group-IB’s technological leadership is built on the company’s 16 years of hands-on experience in cybercrime investigations around the world and 60 000 hours of cybersecurity incident response accumulated in one of the biggest forensic laboratory and a round-the-clock center providing a rapid response to cyber incidents—CERT-GIB. Group-IB is a partner of INTERPOL, Europol, and has been recommended by the OSCE as a cybersecurity solutions provider.
Group-IB’s experience, threat hunting & intelligence have been fused into an eco-system of highly sophisticated software and hardware solutions designed to monitor, identify, and prevent cyber threats.
RELATED STORIES
Cybercriminals are now discussing how to hack IoT devices: Trend Micro