With increased digitalization and cloud migration, the corporate network now extends further out into the Internet — beyond the boundaries and firewalls of an organization. Even the concept of WAN and branch offices is extended. Partners, customers, suppliers, and employees connect to the corporate network from remote locations around the globe. In that sense, it is a borderless network of interconnected networks. That ups the risk for data security, network security, and endpoint security. The threat landscape has broadened to include threats to both, wired and wireless networks. Therefore, when one thinks about network security, it is not just about the security of the internal network, but also that of the extended network.
With more and more software as a service models emerging, demand for security has increased at endpoints and even cloud systems.
To validate its research on the usage of network security solutions, CISO MAG conducted a multiple-choice survey, in the month of February 2020. There were 280 respondents for this survey that included CISOs, COO, CSO, compliance managers, CIOs, CEOs, data protection managers, Director of IT and others.
Here are some key findings of the survey, suggesting the trends in the network security market.
Key Findings:
- Even though the adoption of multiple layers of protection is more than 60%, several organizations rely on Antivirus and Firewall solutions from vendors at 36%.
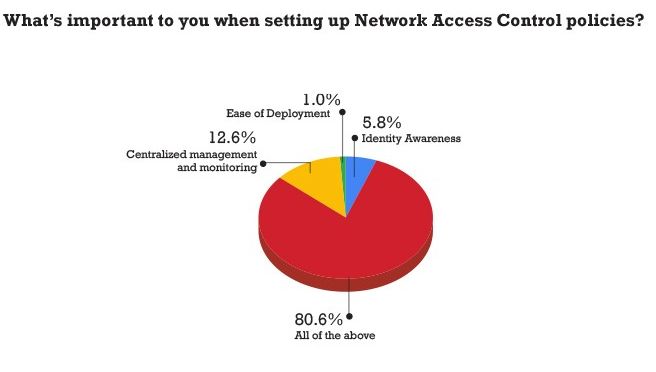
- 6% of respondents suggest using an amalgamation of NAC policies including Identity Awareness, Centralized management and monitoring, and Ease of Deployment
- 5% companies still believe in some sort of a supervision on machine learning solutions on network traffic analysis
- When it comes to Perimeter Security, nearly 30% organizations consider securing Internet, WAN, LAN, and Cloud together
- 35% of respondents suggest that while securing Endpoints the key areas they focus on are Company Owned PCs/Server, Mobile Devices, BYOD, and IoT
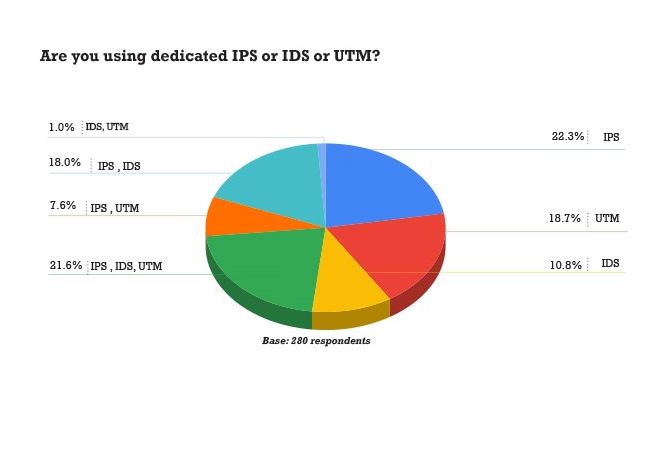
- When it comes to intrusion sensors and modules, IPS tops the chart with 22.3% followed by UTM at 18.7% and IDS at 10.8%
- 7% opt for the hybrid approach for Network Security management 36.6% companies are already using SDN architecture while 63.3% are in the adoption stage
- 6% organizations still consider data security as the biggest security risk in cloud migration
COVID-19 Snap Poll
With the COVID-19 pandemic, organizations across the world are restricting their employees to work from home as part of social distancing to decrease the outbreak. On the flip side, most industry experts state that remote work increases the risks of cyber threats like never before.
To gauge a deeper insight on the precautions companies are taking to combat the threats looming on the cyberspace, CISO MAG also did a snap poll after the survey.
Network security at home
Snap Poll key findings:
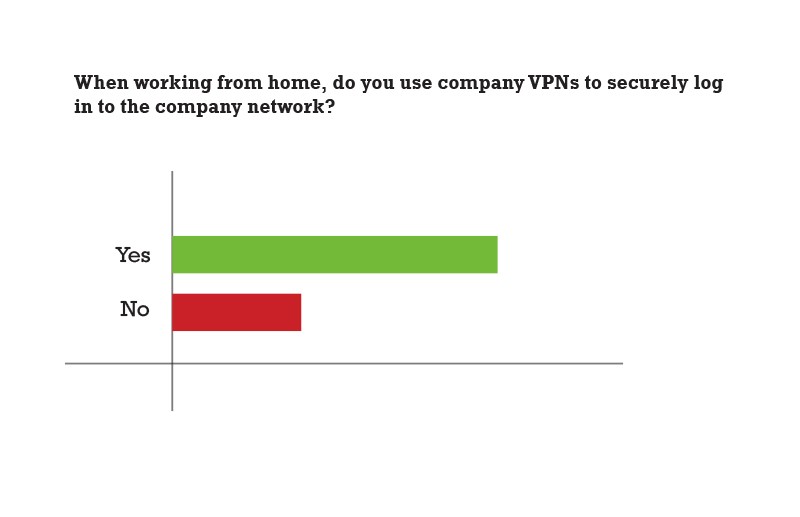
- Only 70% respondents stated that they were using company VPNs to securely log in to the company network while 30% did not.
- Almost all the companies have secured endpoint devices (laptop/ phone) of employees.
- Employees connect to the Internet either using home Wi-Fi connections or hotspot on mobile phone, while nearly 25% use company dongles along with home Wi-Fi and phone hotspot.
Methodology
This survey is based on the results of an online survey that was conducted by CISO MAG readers from EC-Council’s database. The respondents represent a cross-section of organizations from over 56 countries ranging from Argentina, Australia, U.S., U.K., Russia, India, France, Germany, Greece, Indonesia, Italy, Jordan, Kenya, Kuwait, Lebanon, Lithuania and even smaller countries and islands like Malawi, Mali, Nauru. Puerto Rico, Rwanda, Togo, Trinidad and Tobago, among several others. The survey was prepared in consultation with security experts and industry analysts.
Find the full survey report at: bit.ly/cisomagfree
About CISO MAG
CISO MAG is a publication from EC-Council which provides unbiased and useful information to the professionals working to secure critical sectors. The information security magazine includes news, comprehensive analysis, cutting-edge features, and contributions from thought leaders, that are nothing like the ordinary. Within the first year of launch, the magazine reached a global readership of over 50,000 readers. The magazine also has an Editorial Advisory Board that comprises some of the foremost innovators and thought leaders in the cybersecurity space. Apart from this, CISO MAG also presents a platform that reach out to the cybersecurity professionals across the globe through its Summits and Awards and Power List surveys.
About EC-Council
EC-Council, officially incorporated as the International Council of E-Commerce Consultants was formed to create information security training and certification programs to help the very community our connected economy would rely on to save them from a devastating Cyber Attack. EC-Council rapidly gained the support of top researchers and subject matter experts around the world and launched its first Information Security Program, the Certified Ethical Hacker. With this ever-growing team of subject matter experts and InfoSec researchers, EC-Council continued to build various standards, certifications and training programs in the electronic commerce and information security space, becoming the largest cybersecurity certification body in the world.
RELATED STORY
Secure Your Mobile Devices and Wireless Connections When Working From Home