We met Sid Deshpande, Principal Research Analyst at the Gartner Security and Risk Management Summit in Mumbai, in early September. He told us about security spending trends and the growth of security services in India. We also learned about the steps that organizations should take towards making security a part of the development process for applications and platforms. At the end of this interview story he tells us how organizations can protect themselves from ransomware attacks.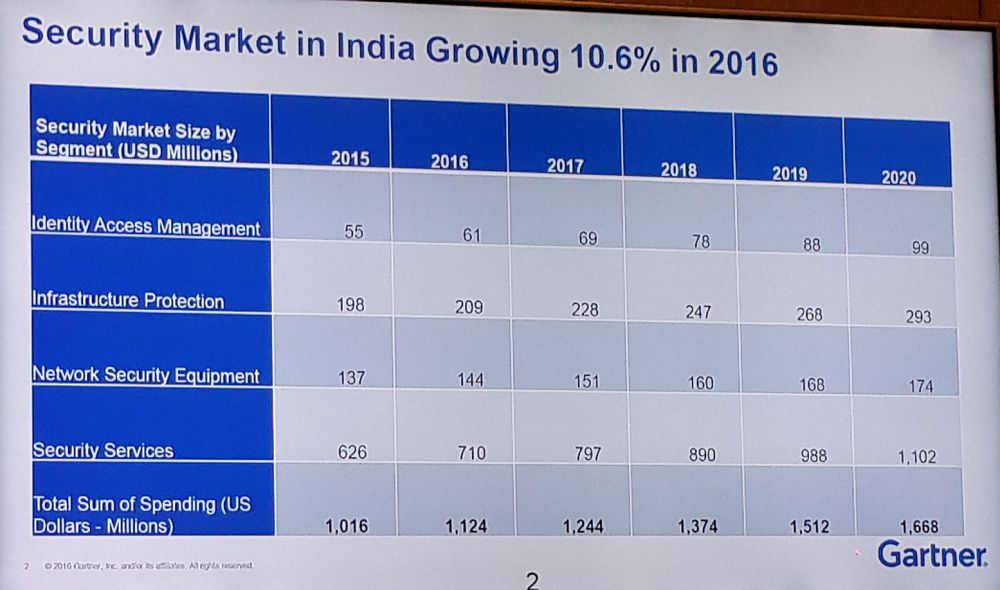
Brian Pereira: According to Gartner, collective Enterprise Security spending in India has increased 10.6 percent – from $1.01 billion in 2015 to $1.12 billion in 2016. And a chunk of this is going towards Security Services. What is causing this shift?
Sid Deshpande: The shift towards services is happening because companies are beginning to realize that they now have to move from just prevention to detection and response.
Services providers are not a substitute for technology; they offer a way to bring on board new technologies and new processes that can assist with detection and response.
So enterprises must use service providers as a seamless part of their security strategy.
Within Security Services, what are the fastest growing segments?
There are three types of Security Services: Security Consulting, Security Implementation and Security Outsourcing.
Implementation has always been a strong market in India and it involves the SIs and VARs (channel). But a lot of the growth is happening in consulting and outsourcing. This is because these providers have established frameworks. They are able to help companies design security strategies, do risk assessments and do other consulting projects around specific areas like Identity Access Management, incident response or forensics. They close the gaps in the company’s enterprise security program.
Outsourcing is more on the operational/execution side. Once you design a security strategy you need to run it. It could either be remotely managed or managed on premise.
In the next 12-18 months we will continue to see security operations being the focal point of this growth in security services.
There is a shortage of skills in India for forensics, incident response and Identity Access Management. Organizations do not have those resources and so they will turn to outsourcing. A service provider can assure a consistent level of service delivery from a skills perspective. By 2020 security outsourcing will be the largest segment in security services.
What is upping the risk factor in organizations and what are the new types of risk?
In the digital world, the CEOs of companies are taking decisions that are based on a technology platform. And that exposes the organization to new types of risks. The employee is now a digital technology user so every employee needs to be digitally aware. And there are new types of risk, not just cloud and mobile.
By 2020 we see 25% of all enterprise traffic will flow outside the enterprise network. Employees are using cloud-based enterprise apps directly from their mobile devices, bypassing the corporate VPN. So how do you secure that? Data has to flow freely to have business value – you can’t lock data. At the same time you need to have intelligence and visibility built into your data flows, so that you are able to monitor the associated risks.
In a digital world it is almost about security having to become an enabler of digital business. Traditionally, the security teams have been very risk averse. The CEOs are born risk takers. But now there is an opportunity for security leaders to change the relationship between them and the business, by becoming enablers of the digital growth story.
Gartner says security should be implemented right at the beginning, during the development stage. How does it fit in with DevOps? To what extent is that happening right now?
We do see this happening in India, especially among those who are adopting Infrastructure as a Service (IaaS). It is usually the developers who are using the IaaS platforms. And developers must bake in the security as they develop the platforms and applications on IaaS.
Platforms like AWS and Azure offer tools that allow developers to embed security into the development process. There is a small minority of organizations where it is happening today. In the broader enterprise context there is still a gap that needs to be bridged.
There is a lot of DevOps that happens inside the organization as well, on the enterprise infrastructure, not on the cloud.
In many cases the developers are actually a part of the business units, and not the security teams. So the security leaders need to embed security professionals from their teams into these development groups for the duration of the development.
The security and developer groups need to work together in order to make DevOps security a reality. It will also create more alignment between IT and the business.
People are the weakest link in the security chain. And now employees are more exposed than ever as they access social media networks at work. Hackers and fraudsters look for company and employee details on these networks and use this information for social engineering and phishing attacks. As a matter of policy, what should organizations be doing to protect employees and information assets?
This has a lot to do with security awareness. A lot of companies have programs for this but it is like a checkbox. Employees take a course and that’s it. What’s lacking is a constant feedback loop between the business owners and security teams around developing a security and risk-aware culture in the organization. It should not just be the business heads, the board of directors or the CEOs who are involved – it also needs to involve the line of business (LOB) managers in this awareness program.
The security team needs to brief them about the risks to the business. They could quantify the risks of a phishing attack in revenue terms, for instance. The LOB heads will then understand it better rather than if you communicate this in security terms.
Involve the business owners into the incident response plan of the company. This is a great way for them to take ownership of their employees and what activities they are doing.
What should we be doing to safeguard ourselves from ransomware and data integrity attacks?
It is extremely important to have a business continuity plan and backup strategy to counter these attacks. There are various technologies that have components on the endpoint or network that you could switch on and enable to combat and detect these threats.
But even before this, organizations need to have a strong vulnerability management program in place. Most of the ransomware attacks exploit commonly known vulnerabilities that were known for a couple of months. There have been few zero-day attacks (new vulnerabilities) using ransomware. The attackers are opportunistic using exploit kits commercially available hacking tools to deploy ransomware, especially on mid-market organizations that do not have a mature vulnerability management program.
So do your patching and vulnerability management right and then look at new technologies and strategies. Do this right and you will be able to defend yourself from 80% of the ransomware attacks.
It reduces your risk exposure significantly.